SIEM stands for security information and event management and provides organizations with next-generation detection, analytics and response. SIEM software combines security information management (SIM) and security event management (SEM) to provide real-time analysis of security alerts generated by applications and network hardware. SIEM software matches events against rules and analytics engines and indexes them for sub-second search to detect and analyze advanced threats using globally gathered intelligence. This gives security teams both insight into and a track record of the activities within their IT environment by providing data analysis, event correlation, aggregation, reporting and log management.
SIEM software can have a number of features and benefits, including:
- Consolidation of multiple data points
- Custom dashboards and alert workflow management
- Integration with other products
How does SIEM work?
SIEM software works by collecting log and event data generated by an organizations applications, security devices and host systems and bringing it together into a single centralized platform. SIEM gathers data from antivirus events, firewall logs and other locations; it sorts this data into categories, for example: malware activity and failed and successful logins. When SIEM identifies a threat through network security monitoring, it generates an alert and defines a threat level based on predetermined rules. For example, someone trying to log into an account 10 times in 10 minutes is ok, while 100 times in 10 minutes might be flagged as an attempted attack. In this way it detects threats and creates security alerts. SIEM’s custom dashboards and event management system improves investigative efficiency and reduces time wasted on false-positives.
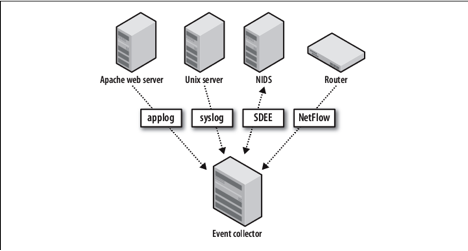
SIEM Capabilities and applications
SIEM has a range of capabilities that, when combined and integrated, offer comprehensive protection for organizations. This is also made easier and more efficient by being brought together into one dashboard. SIEM provides enterprise security by offering enterprise visibility – the entire network of devices and apps.
The software allows security teams to gain attacker insights with threat rules derived from insight into attacker tactics, techniques and procedures (TTPs) and known indicators of compromise (IOC)s. To do this it uses multiple threat intelligence feeds (organized and analyzed information on potential and current threats) which supplements threat detection.
The threat detection element itself can help to detect threats in emails, cloud resources, application, external threat intelligence sources and endpoints. This can include user and entity behavior analytics (UEBA) which analyzes behaviors and activities to monitor for abnormal behaviors which could indicate a threat. It can also detect behavior anomalies, lateral movement and compromised accounts.
This is similar to the security analytics component which detects anomalies in data to derive inform hunting for previously unseen threats.
The managed rules component allows organizations to react almost in real-time to the latest attacker techniques with near real-time updates from analysts.
Once SIEM software determines a threat, vulnerability, attack or suspicious behavior it creates alerts for an organization’s security teams for prompt response. Some versions of the software include workflow and case management to accelerate investigations using automatically generated step-by-step investigation instructions with searches and actions to perform. SIEM alerts can also be customized to fit user needs.
Log management is a complex component of SIEM, comprised of three main areas:
- Data aggregation: gathering vast amounts of data from various applications and databases into one place.
- Data normalization: SIEM allows for all the disparate data to be compared, correlated and analyzed.
- Data analysis/security event correlation: Determining potential signs of a data breach, threat, attack or vulnerability.
SIEM also supports compliance and alert reporting. It helps organizations to simplify compliance reporting with data dashboards to retain and organise event information and monitor privileged user access. This is important because most industrial and governmental regulations (including HIPAA) require some degree of log compilation and normalization, and all require reporting.
Some SIEM solutions, for example FireEye’s, are cloud-based.

SIEM use cases
SIEM has many use cases in the modern threat landscape including detection and prevention for internal and external threats, as well as compliance with various legal standards.
SIEM use in compliance
Tighter compliance regulations are pushing businesses to invest more heavily in IT security and SIEM plays an important role, helping organizations comply with PCI DSS, GDPR, HIPAA and SOX standards. Such compliance mandates are becoming more prevalent and place increased pressure on detecting and reporting breaches. While SIEM was initially used mainly by large enterprises, due to the growing emphasis on compliance and keeping businesses secure, it may be required for small and medium-sized business because regulations such as GDPR, are applicable to organizations irrespective of their size.
IoT security
The Internet of Things (IoT) market is growing. Gartner predicted that there will be 26 billion connected devices by 2020. But with progress comes risk as more connected devices offer more points of entry through which to target businesses because as soon as a hacker is on one part of your network through a connected device, they can access the rest of it very easily. Most IoT solution vendors provide API and external data repositories that can be easily integrated into SIEM solutions. This makes SIEM software and essential part of your business’s cyber security as it can mitigate IoT threats such as DoS attacks and flag at-risk or compromised devices as part of your environment.
Prevention of insider threats
External threats aren’t the only things that make organizations vulnerable, insider threats pose a considerable risk, especially considering the ease of access. SIEM software allows organizations to continuously monitor employee actions and create alerts for irregular events based on ‘normal’ activity. Businesses can also use SIEM to conduct granular monitoring of privileged accounts and create alerts related to actions a given user is not allowed to perform, such as installing software or disabling security software.


